最近在帮加固一个服务器,所以一连发了几个关于服务器的文章。这一篇是安装fail2ban防止暴力破解SSH登陆密码。fail2ban用python编写,通过检测软件日志文件发现账号错误的ip,然后根据设定屏蔽错误超过一定次数的ip。除了SSH之外这个软件还可以保护apache,nginx,ftp,webmail等多个软件账号,还可以自己添加规则。这里只用到了SSH功能。
首先登陆服务器,执行apt-get update升级软件包列表,然后执行apt-get install fail2ban安装fail2ban,等待安装完成。
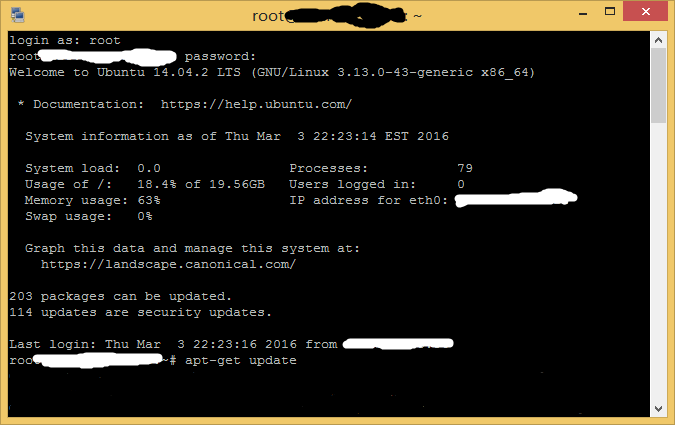
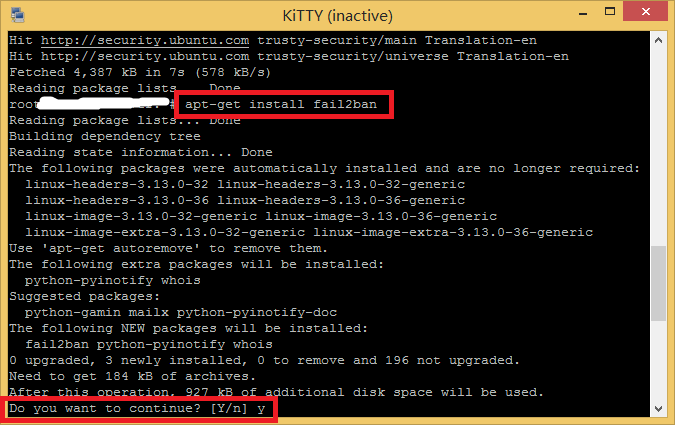
安装完成后,运行vi /etc/fail2ban/jail.conf配置fail2ban。
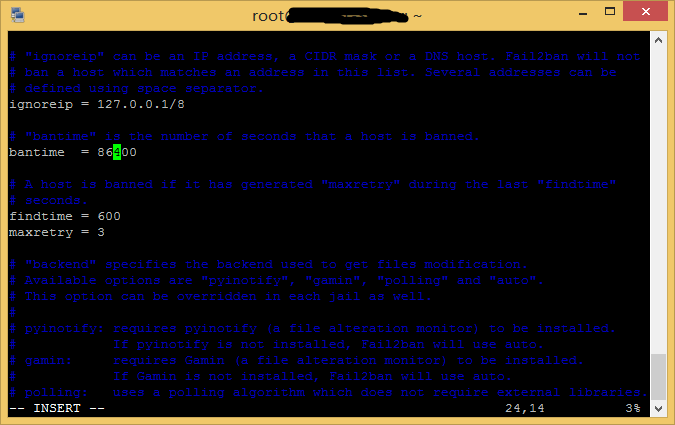
一般需要配置的是屏蔽时间和密码错误次数。按下箭头键到bantime一项,按Insert键进入编辑模式,修改bantime为屏蔽时间,然后按下键头到findtime,修改为需要的值。这三个参数的含义是在findtime时间内连续输入密码错误maxretry次则屏蔽对应ip bantime时间,时间以秒计。修改好之后继续向下翻。
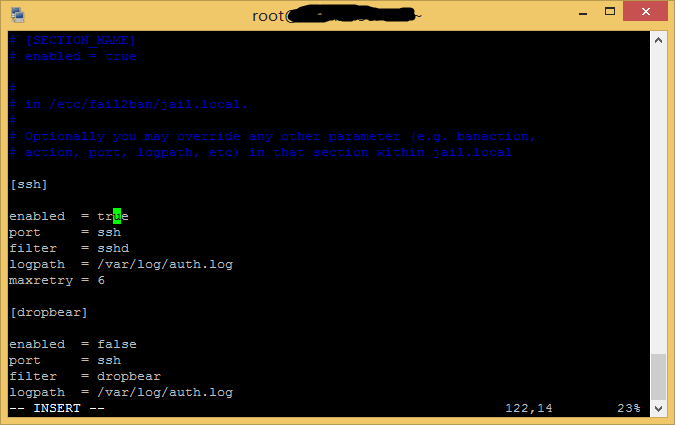
然后翻到[ssh]部分,确保enabled后面是true。然后按Esc键,输入:wq保存退出。然后输入sudo service fail2ban restart并执行,重启fail2ban进程,应用更改后的配置文件。
fail2ban会自动添加开机启动,要测试fail2ban有没有在运行可以输入sudo fail2ban-client ping并运行。如果fail2ban在运行会回应Server replied: pong。然后就可以找个代理,用代理通过ssh登录服务器测试了。不要用常用的ip以防止自己被ban。
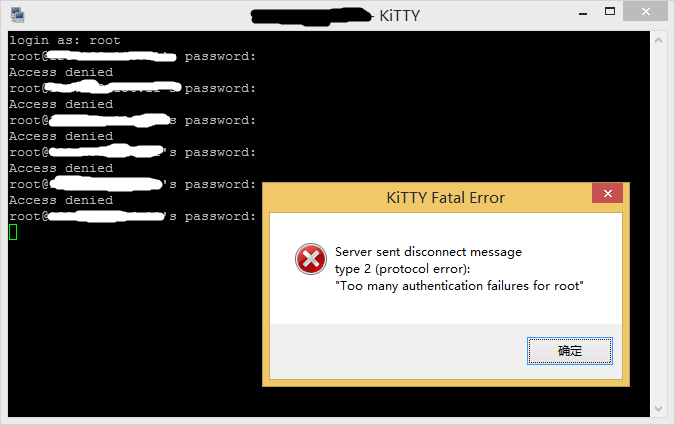
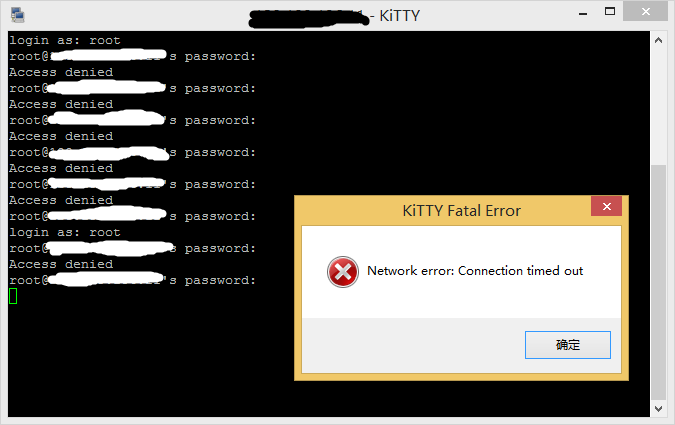

输入几次错误密码之后再登陆时就会连接不上,用另外的ip看iptables已经添加进去被ban的ip了。
附fail2ban配置选项说明。中间省略了一些注释等,对照相应的[***]部分修改即可
[DEFAULT]
# "ignoreip" can be an IP address, a CIDR mask or a DNS host. Fail2ban will not
# ban a host which matches an address in this list. Several addresses can be
# defined using space separator.
//设置不被屏蔽的IP,一般是内网IP,此处不用改
ignoreip = 127.0.0.1/8
# "bantime" is the number of seconds that a host is banned.
//设置屏蔽时间,以秒计
bantime = 86400
# A host is banned if it has generated "maxretry" during the last "findtime"
# seconds.
//设置在多长时间内密码错误次数达到多少次后屏蔽IP,这一项是全局设置,下面还有分程序设置。
findtime = 600
maxretry = 3
# "backend" specifies the backend used to get files modification.
# Available options are "pyinotify", "gamin", "polling" and "auto".
# This option can be overridden in each jail as well.
#
# pyinotify: requires pyinotify (a file alteration monitor) to be installed.
# If pyinotify is not installed, Fail2ban will use auto.
# gamin: requires Gamin (a file alteration monitor) to be installed.
# If Gamin is not installed, Fail2ban will use auto.
# polling: uses a polling algorithm which does not require external libraries.
# auto: will try to use the following backends, in order:
# pyinotify, gamin, polling.
//设置日志文件监视方式,不用改
backend = auto
# "usedns" specifies if jails should trust hostnames in logs,
# warn when reverse DNS lookups are performed, or ignore all hostnames in logs
#
# yes: if a hostname is encountered, a reverse DNS lookup will be performed.
# warn: if a hostname is encountered, a reverse DNS lookup will be performed,
# but it will be logged as a warning.
# no: if a hostname is encountered, will not be used for banning,
# but it will be logged as info.
//对屏蔽的IP进行反向DNS,不用改
usedns = warn
//邮件提醒设置,
#
# Destination email address used solely for the interpolations in
# jail.{conf,local} configuration files.
destemail = root@localhost
#
# Name of the sender for mta actions
sendername = Fail2Ban
//中间不用改
//分程序设置屏蔽参数,格式和全局设置一样
#
# JAILS
#
# Next jails corresponds to the standard configuration in Fail2ban 0.6 which
# was shipped in Debian. Enable any defined here jail by including
#
# [SECTION_NAME]
# enabled = true
#
# in /etc/fail2ban/jail.local.
#
# Optionally you may override any other parameter (e.g. banaction,
# action, port, logpath, etc) in that section within jail.local
[ssh]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 3